Win 7 Security 2013 trojan comes from FakeRean virus family, also known as Braviax or MultiRogue 2013. This is a type of Trojan that secretly penetrates into the vulnerable computer system and installs the fake anti-virus program. The name of this program depends on the type of the operating system installed on the computer. The badware intends to persuade the potential victim that the computer is suffers from serious virus invasion and requires immediate anti-virus help. To remove all unwanted items you are offered to buy the commercial version of Win 7 Security 2013. Knowing all the facts or at least the basis information about this malicious application is the first step on the ladder of its successful removal from your computer.
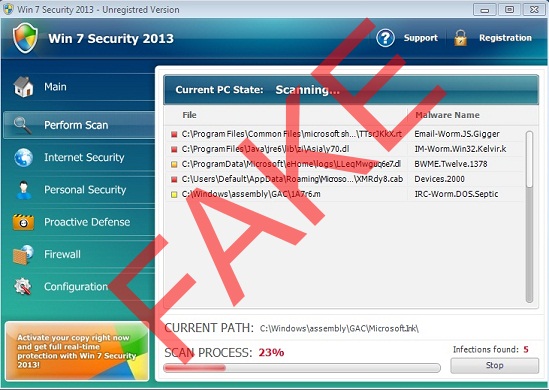
Win 7 Security 2013 does its best to wind you round and rip you off. At once upon penetration, it changes your system parameter to be started automatically, with every Windows login. So you will see its GUI after every computer reboot. First, it will launch the fake system checkup and then presents invented detection list. All these allegedly spotted viruses, rogues, Trojans do not reside on your system. It is an illusion only. Just as we’ve already said, these fake scans are initiated each time you switch the PC on. It aims to make the users panic seeing the bunch of fictitious info. Thus do not treat any word of this parasite seriously. The only thing you should do without lingering is the removal of this virus by means of the reputable anti-virus solution. The effective removal of this parasite is available for you by means of GridinSoft Trojan Killer. The step-by-step removal guide is stipulated in the section below. Be careful to follow all instructions to successful kill the virus.
Similar removal video guide:
Win 7 Security 2013 removal instructions from GridinSoft Trojan Killer anti-virus Lab
Step 1.
Run GridinSoft Trojan Killer:
Click Win+R and type the direct link for the program's downloading  If it does not work, download GridinSoft Trojan Killer from another uninfected machine and transfer it with the help of a flash drive.
If it does not work, download GridinSoft Trojan Killer from another uninfected machine and transfer it with the help of a flash drive.
Step 2.
Install GridinSoft Trojan Killer.
Right click - Run as administrator.

IMPORTANT!
Don’t uncheck the Start Trojan Killer checkbox at the end of installation!

Manual removal guide of Win 7 Security 2013 virus:
Delete Win 7 Security 2013 files:
- %LocalAppData%\[rnd_2]
- %Temp%\[rnd_2]
- %UserProfile%\Templates\[rnd_2]
- %CommonApplData%\[rnd_2]
Delete Win 7 Security 2013 registry entries:
- HKEY_CURRENT_USER\Software\Classes\.exe
- HKEY_CURRENT_USER\Software\Classes\.exe\ [rnd_0]
- HKEY_CURRENT_USER\Software\Classes\.exe\Content Type application/x-msdownload
- HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon
- HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon\ %1
- HKEY_CURRENT_USER\Software\Classes\.exe\shell
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command\ “[rnd_1].exe” -a “%1″ %*
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command\IsolatedCommand “%1″ %*
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command\ “%1″ %*
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command\IsolatedCommand “%1″ %*
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\ Application
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\Content Type application/x-msdownload
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\DefaultIcon
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\DefaultIcon\ %1
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell\open
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell\open\command
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell\open\command\ “[rnd_1].exe” -a “%1″ %*
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell\open\command\IsolatedCommand “%1″ %*
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell\runas
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell\runas\command
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell\runas\command\ “%1″ %*
- HKEY_CURRENT_USER\Software\Classes\[rnd_0]\shell\runas\command\IsolatedCommand “%1″ %*
No comments:
Post a Comment